Webinar
Think About Your Audience Before Choosing a Webinar Title

Sponsored by ShiftLeft
What You’ll Learn in This Webinar
JavaScript is arguably the most important modern programming language, but despite its massive popularity, it is inherently very difficult to secure. As a dynamically typed and interpreted programming language, static analysis of JavaScript source code is very limited in how it can analyze data-flow. However, code property graphs offer new ways to reconstruct data-flows in dynamic languages via detailed annotations.
A foundational concept of data-flow security analysis is modeling the values that can appear at runtime. However, dynamic types in JavaScript means that an analysis must be able to handle variables that can contain values of different types (e.g. string and/or integers), at different points during execution. JavaScript further complicates this by supporting a myriad of coercions between types. The following JavaScript program illustrates a case where multiple types come into play for a single variable:
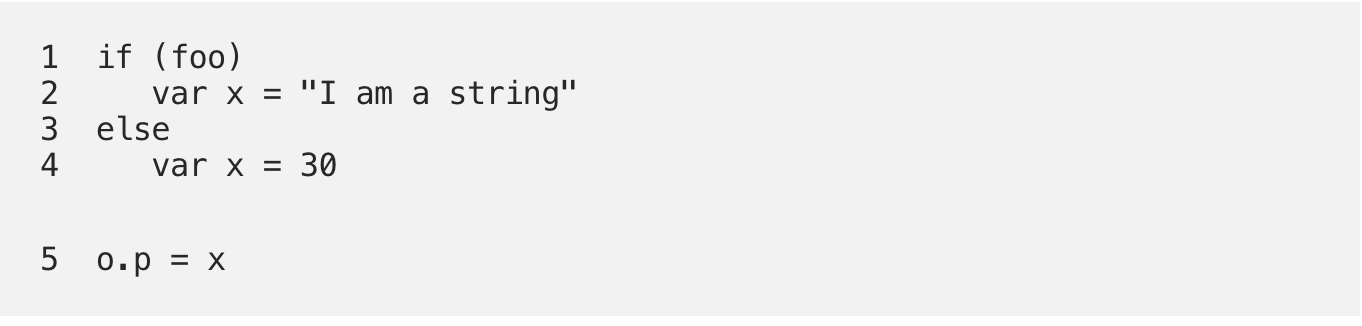
In the above example the value of x depends on the boolean value foo. If the value of foo is not known, then x can be either a string or an integer when assigned to the property. For the analysis to be useful we must track both possibilities.
This technical webinar will cover the following challenges of analyzing JavaScript Source Code, as well as discuss how code property graphs can be used to close the gaps:
- Server Side JavaScript Landscape
- State of Vulnerabilities in Server Side JS
- Why vulnerability discovery is hard with JS (untyped languages)
- Introducing CPG and taint flow analysis of JS using CPG
- Illustrative walk through of OWASP use cases
- Demo